Zhihuang Liu is a Ph.D. candidate at the College of Computer Science and Technology, National University of Defense Technology (NUDT), with an expected graduation date of June 2026.
Research interests: Privacy Protection, Applied Cryptography, Usable Security, Large Language Models (LLMs), and Artificial Intelligence (AI) Security.
High self‑motivated researcher in Privacy Protection and Applied Cryptography with focus on AI Security and Usable Security solutions.
📖 Educations
- 2023.09 - now, Ph.D. Candidate, National University of Defense Technology (Double First-Class 双一流, Project 985), Changsha, China.
- 2020.09 - 2023.06, Master, Fuzhou University (Double First-Class 双一流, Project 211), Fuzhou, China.
- 2016.09 - 2020.06, Bachelor, Fuzhou University (Double First-Class 双一流, Project 211), Fuzhou, China.
🎉 News
- 2025.10: An effort on Security Vulnerabilities in Self-Hosted LLM Services has been submitted to WWW2026 (Core A*, CCF A). Wish us luck!
- 2025.08: One paper has been accepted by IEEE Transactions on Circuits and Systems for Video Technology (CCF B, JCR Q1, IF:11.1, 中科院一区TOP).
- 2025.05: A paper titled Risk-Aware Privacy Preservation for LLM Inference has been submitted to TIFS (CCF A, JCR Q1, IF: 8.0, 中科院一区TOP) for consideration. Wish us luck!
- 2025.03: One paper has been accepted by IEEE Transactions on Circuits and Systems for Video Technology (CCF B, JCR Q1, IF:11.1, 中科院一区TOP).
- 2025.03: One paper has been accepted by IEEE Transactions on Big Data (CCF C, JCR Q1, IF:5.7, 中科院二区).
- 2024.12: Awarded the Ourstanding Student of NUDT.
- 2024.12: Awarded China National Scholarship for PhD Students.
- 2024.09: One paper has been accepted by IEEE Symposium on Security and Privacy (SP’25) (Top‑tier security conference, Ranked No. 1, Core A*, CCF A, AR: 14.8% (257/1740)).
- 2024.08: One paper has been accepted by International Conference on Neural Information Processing (CCF C).
- 2024.04: One paper has been accepted by IEEE Transactions on Information Forensics and Security (CCF A, JCR Q1, IF: 8.0, 中科院一区TOP).
- 2023.12: One paper has been accepted by Future Generation Computer Systems (FGCS) (CCF C, JCR Q1, IF:6.1, 中科院一区TOP).
📝 Selected Publications (* Corresponding author)
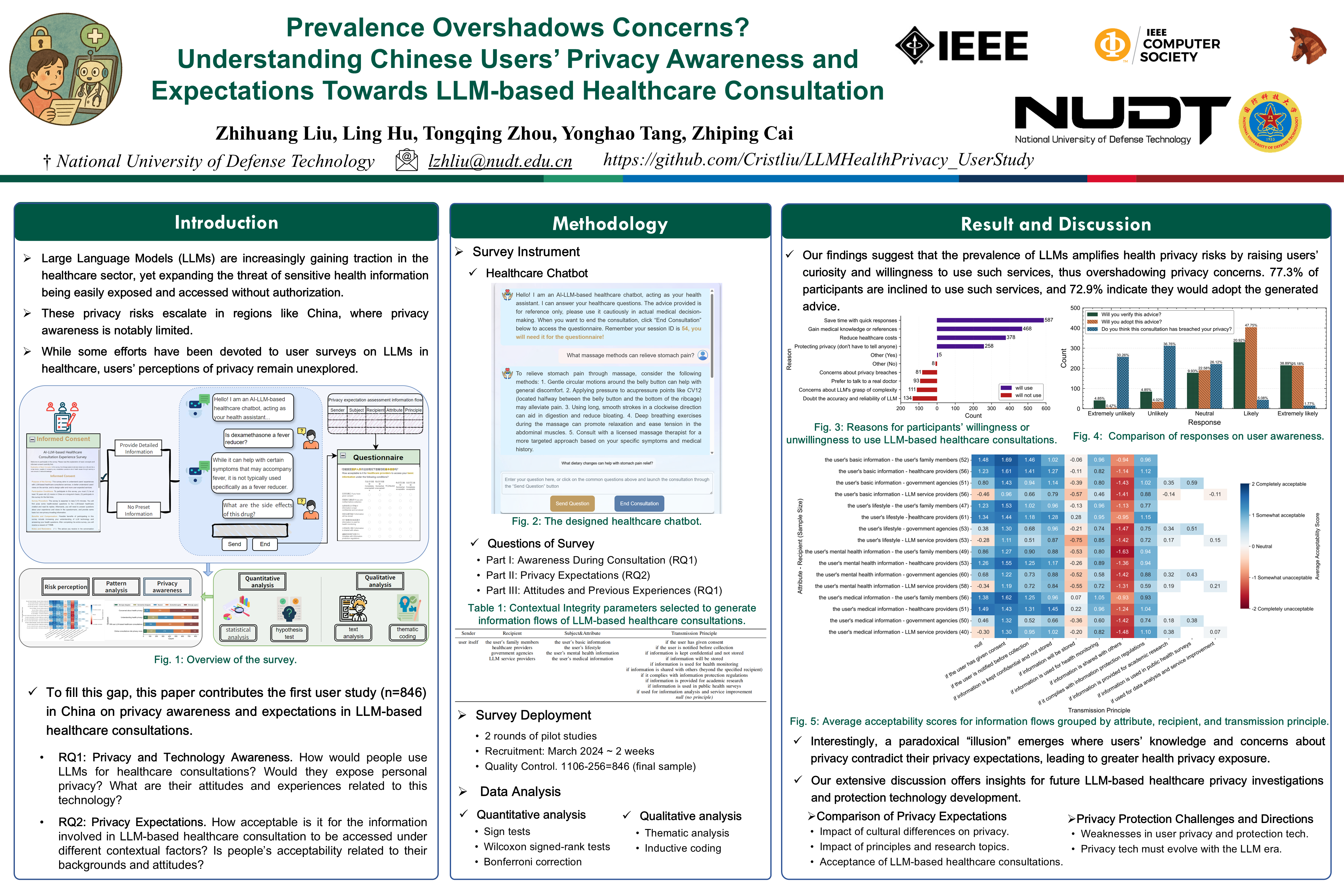
Prevalence Overshadows Concerns? Understanding Chinese Users’ Privacy Awareness and Expectations Towards LLM-based Healthcare Consultation
Zhihuang Liu, Ling Hu, Tongqing Zhou, Yonghao Tang, Zhiping Cai*
The 46th IEEE Symposium on Security and Privacy (S&P25) [Paper] [PDF] [Project] [Code]
- This paper contributes the first user study (n=846) in China on privacy awareness and expectations in LLM-based healthcare consultations.
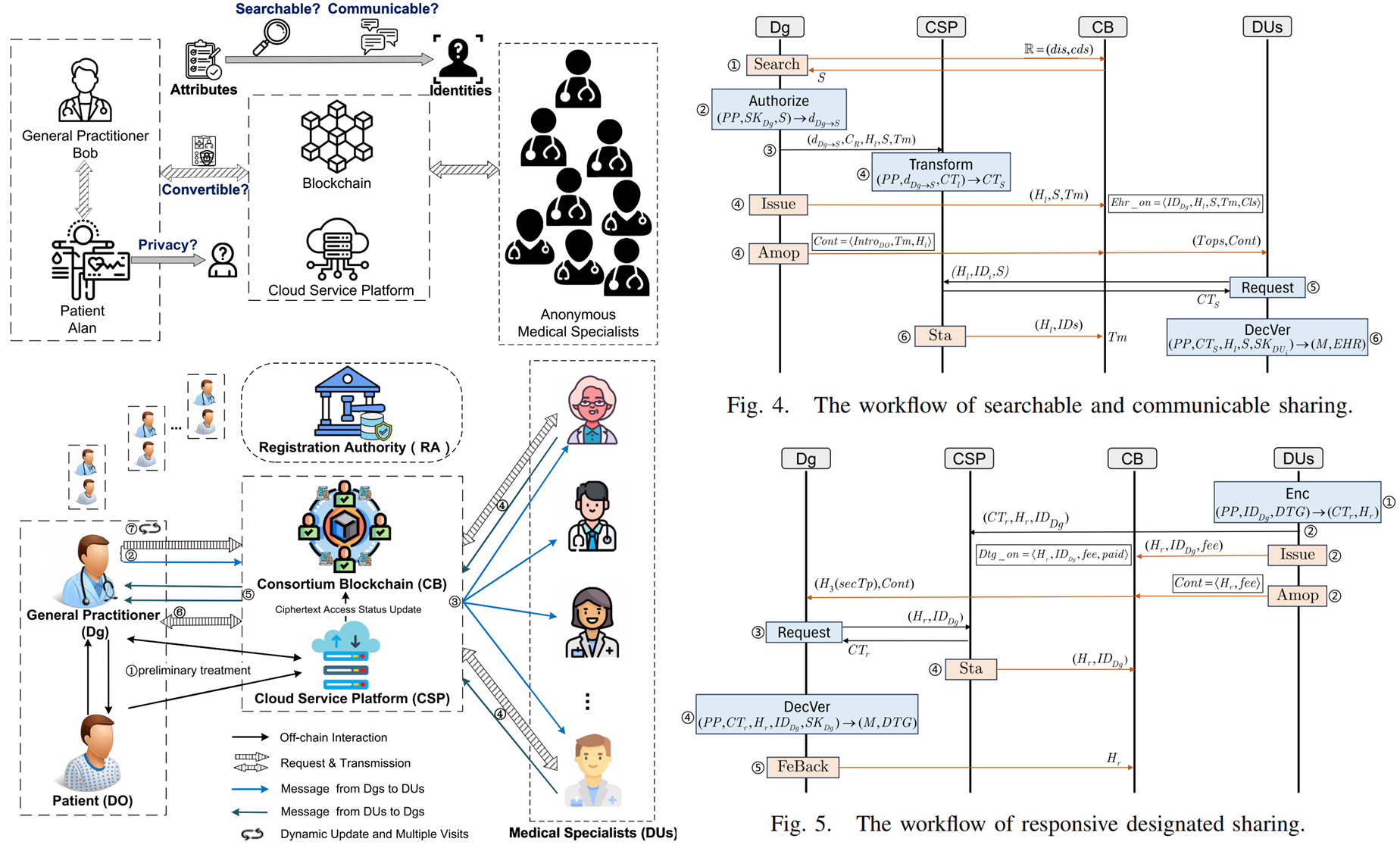
SeCoSe: Toward Searchable and Communicable Healthcare Service Seeking in Flexible and Secure EHR Sharing
Zhihuang Liu, Ling Hu, Zhiping Cai*, Ximeng Liu, and Yanhua Liu
IEEE Transactions on Information Forensics and Security [Paper] [PDF] [Project] [Code]
- This Paper proposes a searchable and communicable proactive healthcare service seeking scheme (SeCoSe) in a blockchain-based EHR sharing system.
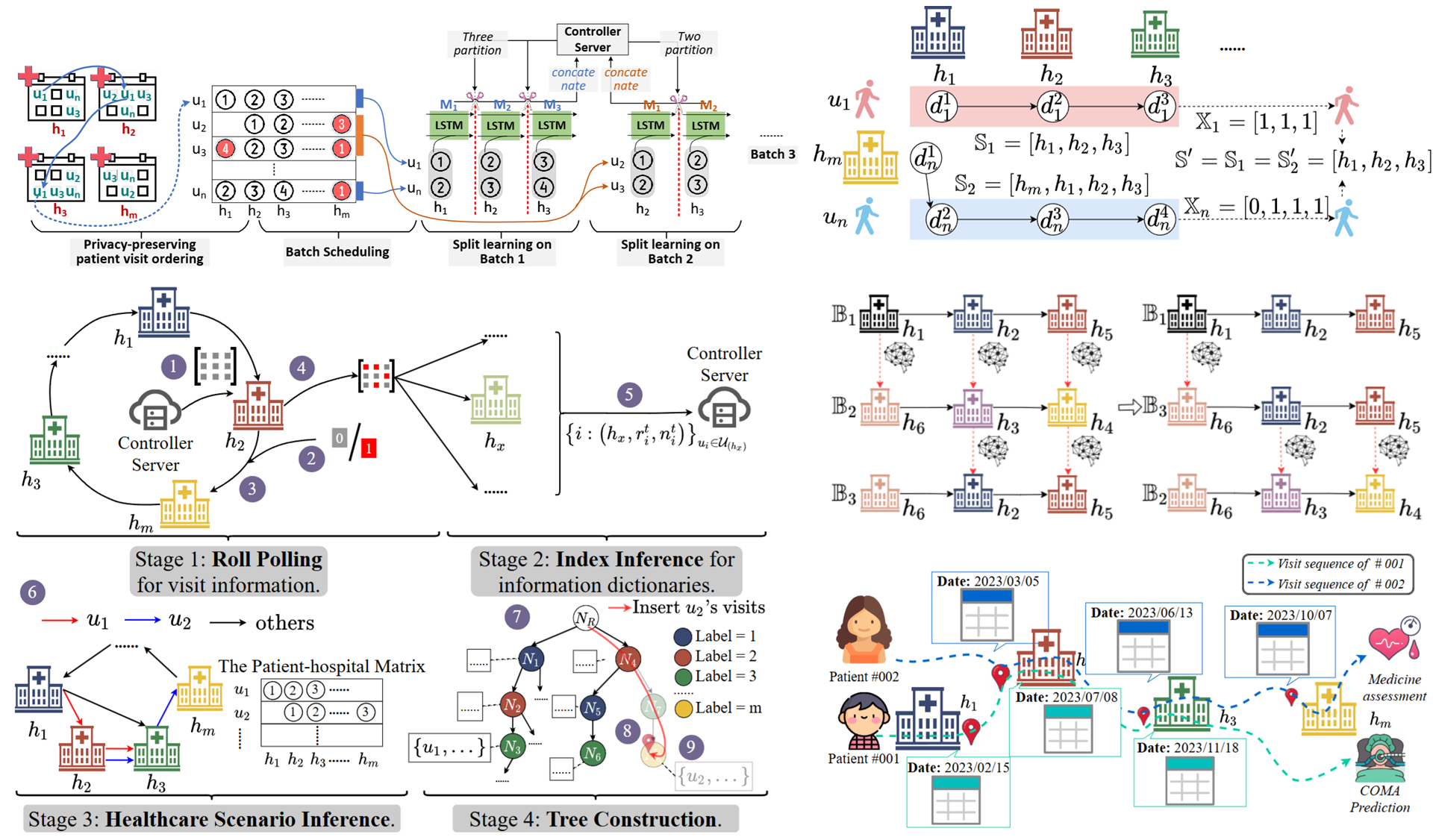
Split Learning on Segmented Healthcare Data
Ling Hu, Tongqing Zhou, Zhihuang Liu*, Fang Liu, and Zhiping Cai*
IEEE Transactions on Big Data [Paper] [PDF] [Project] [Code]
- This paper first investigates the privacy-preserving learning problem on segmented healthcare data. Considering the data split situation, we propose to adapt split learning to support the distributed learning process and design a novel framework STSL (i.e., Spatio-temporal Split Learning).
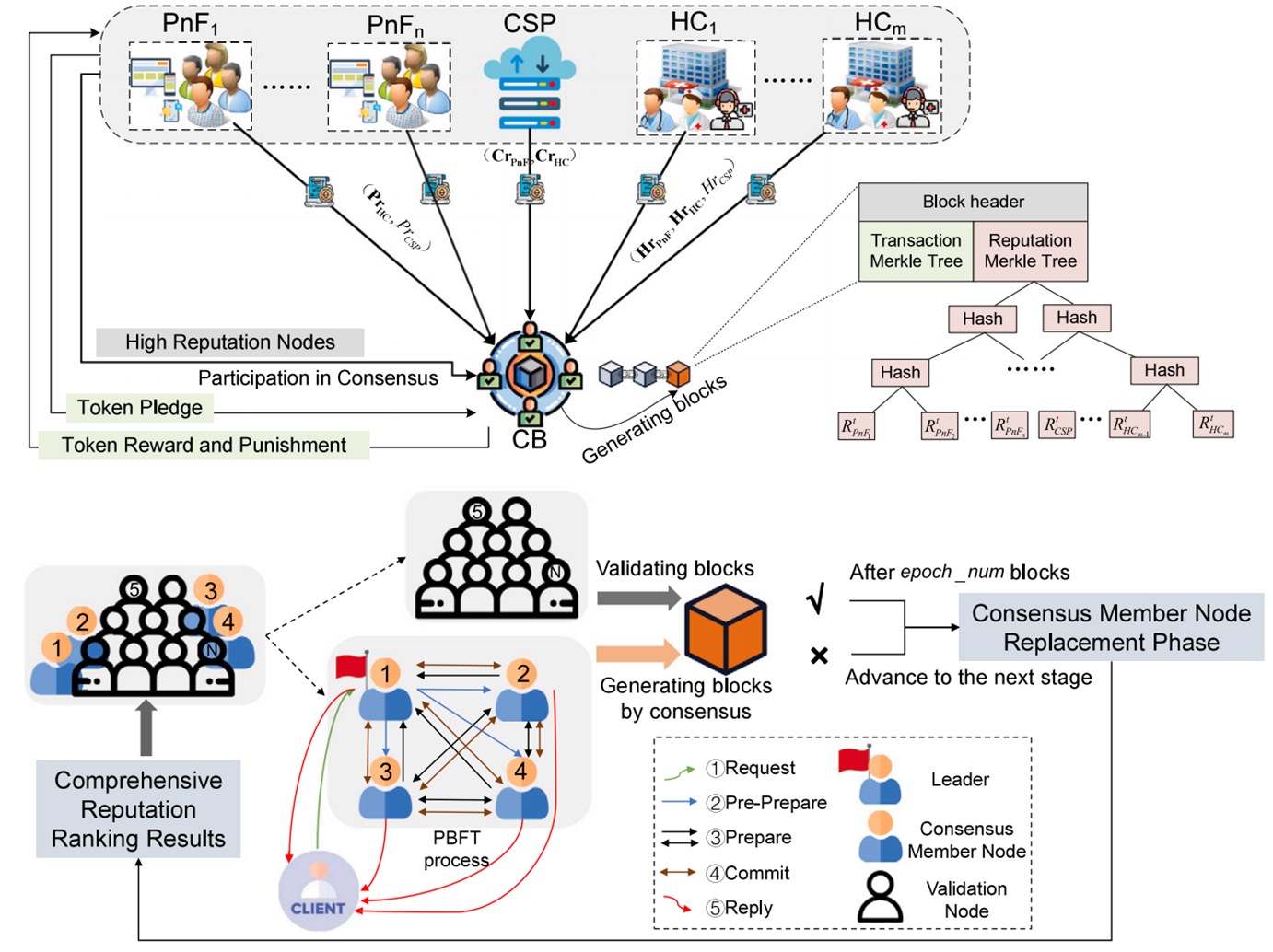
Blockchain and trusted reputation assessment-based incentive mechanism for healthcare services
Yanhua Liu (~Supervisor~), Zhihuang Liu*, Qiu Zhang, Jinshu Su, Zhiping Cai, and Xiaoyan Li
Future Generation Computer Systems [Paper] [PDF] [Project] [Code]
- This Paper proposes a Blockchain and trusted Reputation assessment-based Incentive mechanism for healthcare services (BtRaI).
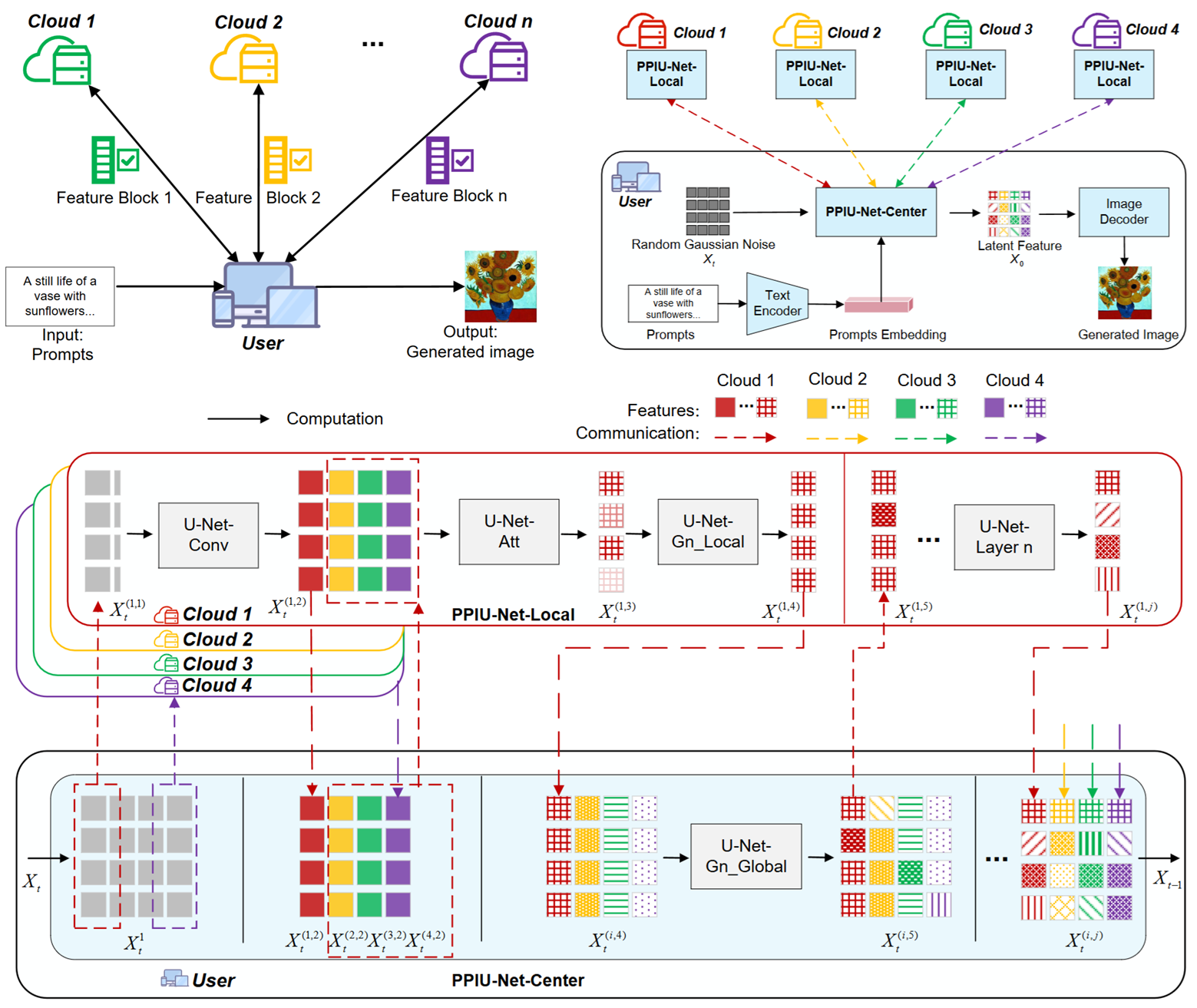
PPIDM: Privacy-Preserving Inference for Diffusion Model in the Cloud
Zhangdong Wang, Zhihuang Liu, Yuanjing Luo, Tongqing Zhou*, Jiaohua Qin, and Zhiping Cai*
IEEE Transactions on Circuits and Systems for Video Technology [Paper] [PDF] [Project] [Code]
- This paper proposes PPIDM (Privacy-Preserving Inference for Diffusion Models), a novel framework for diffusion model inference in cloud environments that mitigates both resource constraints and privacy risks.
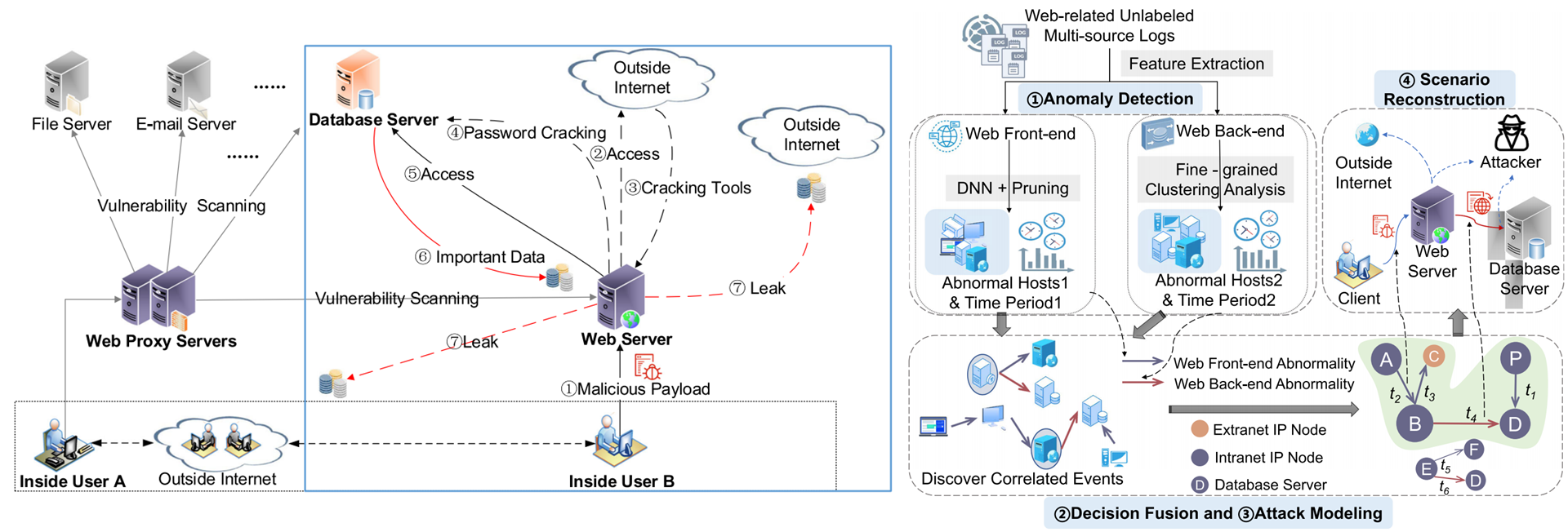
A Web Back-End Database Leakage Incident Reconstruction Framework Over Unlabeled Logs
Yanhua Liu (~Supervisor~), Zhihuang Liu*, Ximeng Liu, and Wenzhong Guo
IEEE Transactions on Emerging Topics in Computing [Paper] [PDF] [Project] [Code]
- This paper proposes a web back-end database leakage incident reconstruction framework (WeB-DLIR) over unlabeled logs, designed to improve the intelligence and automation of reconstructing web back-end database leakage incidents triggered by web-based attacks in unannotated logging environments.
🗂️ Selected Projects
- [2023.09-2025.10] National Key Research and Development Program of China (国家重点研发项目): Research on Feature Extraction and Secure Computing Framework of Clinical Big Data for Drug R&D.
- [2022-2023] Fujian FuHaiChuang Petrochemical (福建福海创石油化工有限公司委托): Research and Development of Cyberspace Security Science and Technology.
- [2021-2022] State Grid Corporation of China (国家电网信通亿力科技公司委托): Research and Development of Survivability Analysis Technology for Data Network Systems.
- [2020-2021] Chinese Academy of Sciences (中国科学院信息工程研究所委托): Prototype System for Abnormal Traffic Visualization and Analysis.
🔖 Patents
- [2024.08, China] User Privacy Awareness Observation Device and Method for LLM‑based Healthcare Consultation, CN118629560A.
- [2023.12, China] Anonymous Service Retrieval and Sharing Method, Apparatus, and Device for Healthcare Blockchain, CN117610077A.
- [2022.08, China] A Web Security Incident Forensics Method and System for Data Leakage, ZL 2021 1 0879142. X.
- [2024.12, China] A Multi‑Party Constrained Privacy Visualization Method, Apparatus, and Device for Medical Data Sharing, ZL 2024 1 1089681.3.
- [2024.11, China] Distributed Time‑Sequential Data Split Learning Method, Apparatus, and Computer Device, ZL 2024 1 1089563.2
- [2024.11, China] Privacy‑Preserving Sorting Method, Apparatus, and Computer Device for Multi‑Institution Time‑Sequential Data, ZL 2024 1 1089805.8.
- [2024.10, China] Generative AI‑Based Polymorphic‑Sensitive Puzzle Detection Method, Apparatus, and Device, ZL 2024 1 1089891.2.
🎖️ Honors and Awards
- [2024.12] Outstanding Student, National University of Defense Technology. (优秀学员)
- [2024.12] National Scholarship, Ministry of Education, China. (博士研究生国家奖学金)
- [2024.08] Excellent Master Thesis, Fuzhou University. (优秀硕士论文)
- [2023.08] Special Award in Master Comprehensive Scholarship, Fuzhou University. (硕士综合学业奖学金特等奖)
- [2023.06] Excellent Graduate, Fuzhou University. (优秀毕业生)
- [2023.02] Third Prize (National), CCF Big Data & Computing Intelligence Contest. (CCF大数据与计算智能大赛全国三等奖)
- [2022.11] National Scholarship, Ministry of Education, China. (硕士研究生国家奖学金)
- [2020.12] Special Award for Outstanding New Student Scholarship, Fuzhou University. (优秀新生特等奖学金)
- [2020.10] Third Prize (National), China Collegiate Computig Contest. (中国高校计算机大赛三等奖)
- [2020.06] Excellent Graduate, Fuzhou University. (优秀毕业生)
- [2019.12] National First Prize (Team Leader & Key Contributor), CCF Big Data & Computing Intelligence Contest. (CCF大数据与计算智能大赛全国一等奖)
👐🏼 Services
Journal Reviewer
- IEEE Transactions on Dependable and Secure Computing (TDSC), IEEE Transactions on Wireless Communications (TWC), IEEE Transactions on Systems, Man, and Cybernetics: Systems (TSMC)
- IEEE Internet of Things Journal (IOTJ), SCIENCE CHINA Information Sciences (Chinese), Journal of Parallel and Distributed Computing (JPDC)
- The Journal of Supercomputing, Software Quality Journal, Scientific Reports, International Journal of Machine Learning and Cybernetics
Conference Reviewer (Program Committee)
- The Annual Conference on Neural Information Processing Systems (NeurIPS), The IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), The Association for the Advancement of Artificial Intelligence (AAAI)
- The International Joint Conference on Artificial Intelligence (IJCAI), ACM International Conference on Multimedia (MM)
Invited Talks
- 2024.09, Excellent Doctoral Student Forum, Xiamen, Organized by Xiamen University.
Teaching Assistant
- Undergraduate thesis supervision
- Course: Network Management
Policy Report
- Conducted comprehensive analysis on the deployment risks associated with localizing large language models. Authored a policy brief on Analysis and Countermeasures for xxxx Localized Deployment of Open‑Source Large AI Models. The resulting report was submitted to a National Ministry (呈报至某国家部委), informing high‑level decision‑making.
Cyber Security Audit & Report
- Identified critical Jailbreak Vulnerabilities in a LLM‑based Intelligent Assistant integrated within a National Demonstration Center of Experimental Computer Education (某计算机国家级实验教学示范中心). Conducted scanning on the website, revealing multiple high‑risk, web‑related vulnerabilities (e.g., Cross‑Site Scripting, SQL Injection) that could result in sensitive data exposure and malicious database manipulation. Promptly reported findings to the center’s authority for immediate mitigation.
📬 Contact
Email: lzhliu@nudt.edu.cn
WeChat: